Microsoft LAPS Support

Dear JDisc friends,
we understand that storing your crown jewels (administrative accounts and passwords) in products like JDisc Discovery is not something that IT security departments really like. There is always the conflict between being as secure as possible and getting current inventory information (which often requires administrative accounts). Therefore, we implemented on request from several customers integrations with password management tools. So far, we have implemented integrations with CyberArk (check out our integration page) and Thychotic.
The integrations all work in a similar way. The device passwords are no longer stored in JDisc Discovery’s database but stay within the password management tool. Whenever JDisc Discovery needs a username and password to scan a computer, it queries the password manager via its APIs for the current password. The password is not getting stored within JDisc Discovery’s database at all. And this is also pretty convenient for another reason. Most of the password management tools can rotate passwords on a regular basis (e.g. change the passwords each day). This would make the use of JDisc Discovery nearly impossible since you cannot manually change the passwords within the discovery every day.
Now, we have added Microsoft LAPS (Local Administrator Password Solution) to the list of supported solutions. Microsoft LAPs works slightly differently compared to CyberArk and Thycotic. Microsoft LAPS changes the local built-in administrator password for all computers within a directory individually and can be scheduled to change it on a regular basis. Microsoft LAPS stores the current password for each computer within the Active Directory as a property and the password can be queried (of course in a secure manner) via LDAP queries.
In order to configure Microsoft LAPS within JDisc Discovery, you need to tell the discovery which directory objects are configured with LAPS. Therefore, we have added a new configuration tab within the scope section in the discovery configuration dialog.
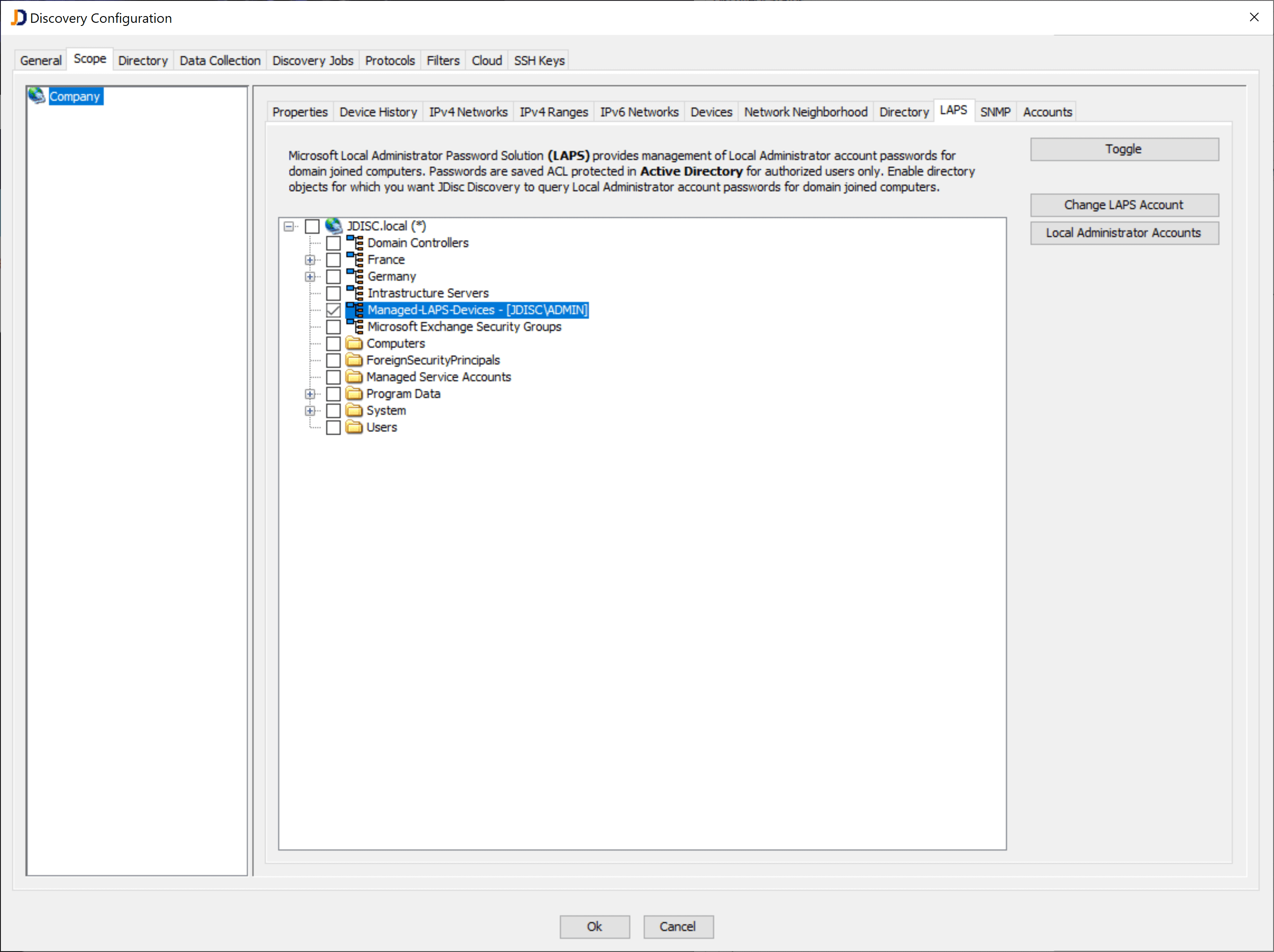
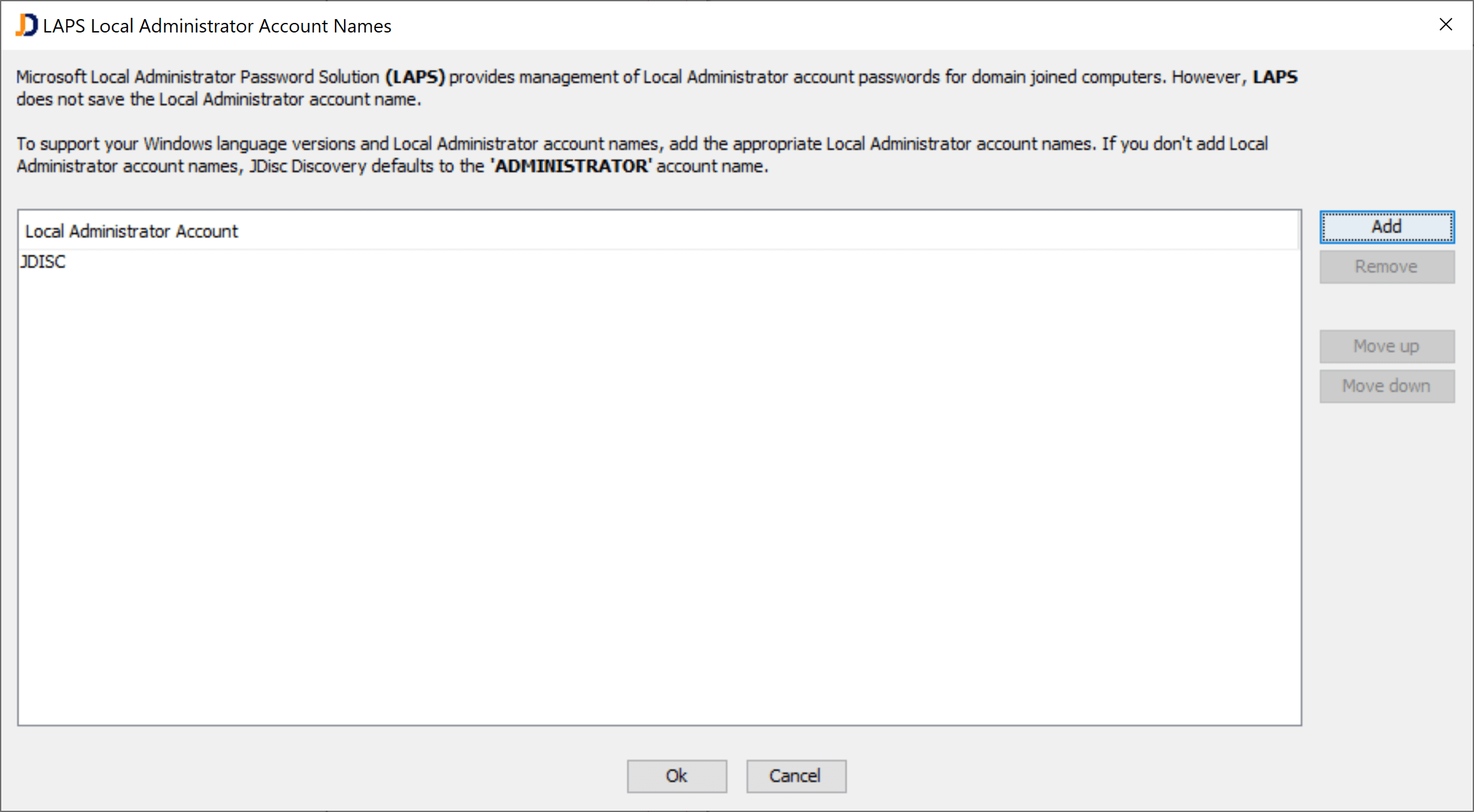
You need to enable an organizational unit or other directory object for LAPS and configure a LAPS account. The LAPS account is being used to query the current password for a computer within this directory. Since the name for the local administrator (usually ADMINISTRATOR) can change based on the localization or changed on purpose, we also need to be able to define one or more logins for the local administrator. Unfortunately, LAPS only stores the local administrator’s password, but not the login within the AD properties.
Click on the Local Administrator Accounts button in order to provide a list of local admin accounts.
Once those configurations have been completed, JDisc Discovery will use LAPS when it detects a computer within a LAPS-enabled directory. First, it uses the LAPS account to query the computer’s current password. Then it uses this password together with the defined list of logins to check connectivity. JDisc Discovery uses the login ADMINISTRATOR when there are no individual accounts configured.
Similar to the other password manager tools, JDisc Discovery never stores any local administrator password within its database.
We hope you like this new feature and hopefully, those security-related features help to become best friends with your security departments 🙂
The LAPS feature will be released with build 5084.
Cheers,
Thomas
