Using non-administrative accounts to discover Windows computers


Dear JDisc user,
have you already been asked by your IT security department not to use local or domain users with administrator rights on Windows computers for network discovery?
Unfortunately, Windows doesn’t offer Linux-like privilege elevation methods like SU or SUDO. Of course, security folks want you to embrace the principle of least privilege (PoLP) everywhere – including network discovery.
Discovering Windows computers with non-administrative accounts requires a lot of configuration work, including changing DCOM and WMI security settings, user group assignments, firewall rules to allow inbound traffic over ephemeral ports for WMI, and so on. If you’ve ever tried this, you probably know that it’s very time-consuming and error-prone.
That’s why we at JDisc have implemented a solution that simplifies the problem of discovering Windows computers with non-administrative users (local or domain) for you.
Starting with Build 5132 you can install and configure our JDisc Discovery Zero-Footprint Agent on Windows computers with your own software distribution or simply manually. From the command line, you can specify the users or user groups that are allowed to discover Windows computers with elevated privileges.
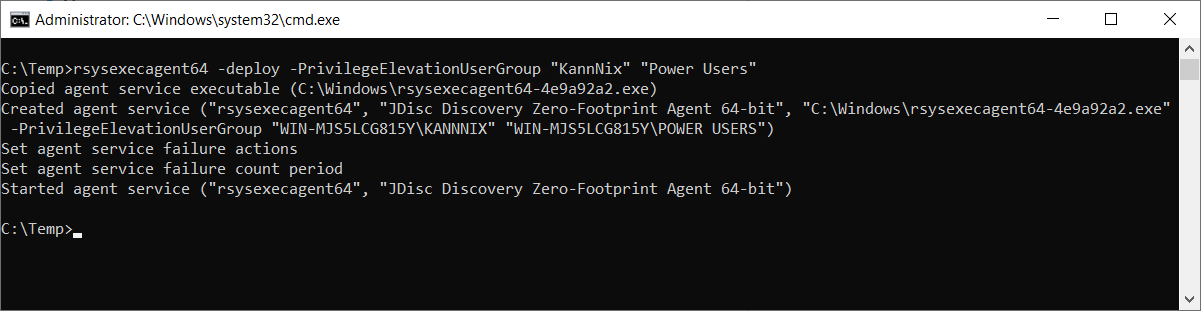
For a more detailed description, please checkout chapter 3.2.1.3 Permanent Installation / Uninstallation of our Security Whitepaper.
Please make sure the SMB protocol is enabled and port TCP/445 is open for inbound network traffic. This is not new and has always been required to communicate with the JDisc Discovery Zero-Footprint Agent (Windows Remote Login).
Last but not least, don’t forget to add/configure non-administrative user accounts for your Windows computers in the JDisc Discovery user interface.
Cheers, Thomas
