Security Add-On: SSH Cipher, MAC, and Key-Exchange Algorithms

Dear JDisc users,
As usual, we are constantly enhancing our data collection capabilities. This time, we have enhanced our security add-on to collect information about the SSH cipher, MAC, and key-exchange algorithms.
When the security add-on is installed and licensed, the discovery configuration dialog offers a new setting for security-related data collections.
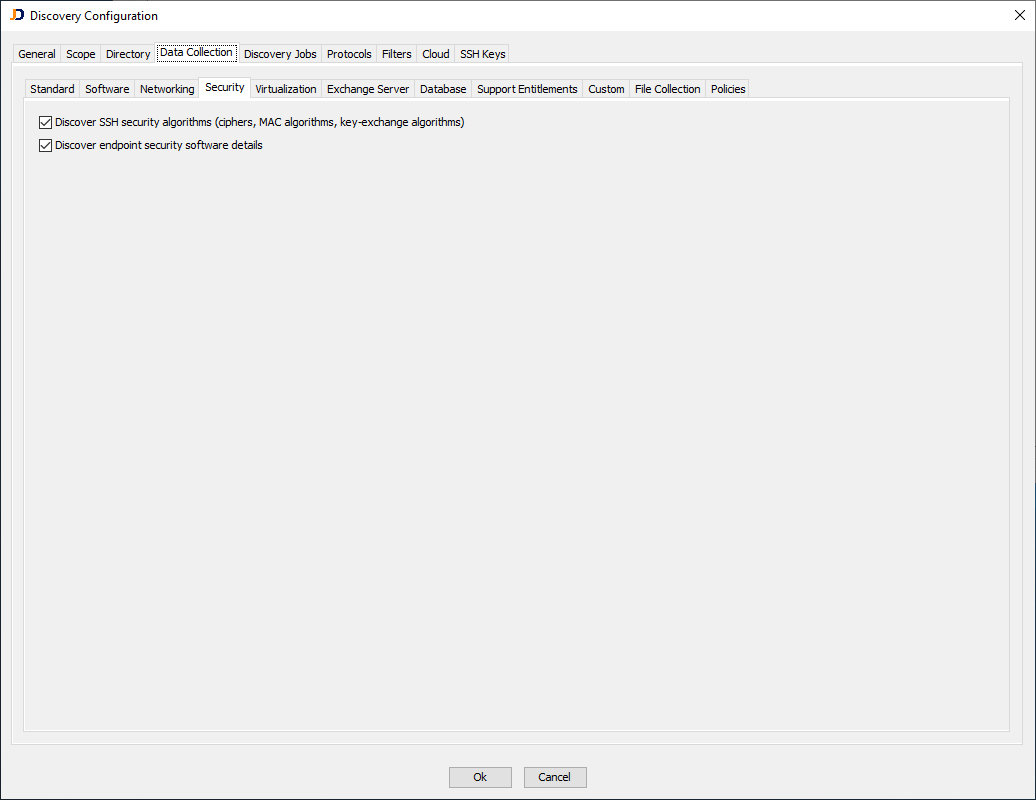
When JDisc Discovery detects the SSH server on a device, then we will collect the following information:
- the list of available ciphers on the remote device
- the list of available mac algorithms on the remote device
- the list of available key-exchange algorithms on the remote device
- the cipher used for the actual connection
- the mac algorithm used for the actual connection
- the key-exchange algorithm used for the actual connection
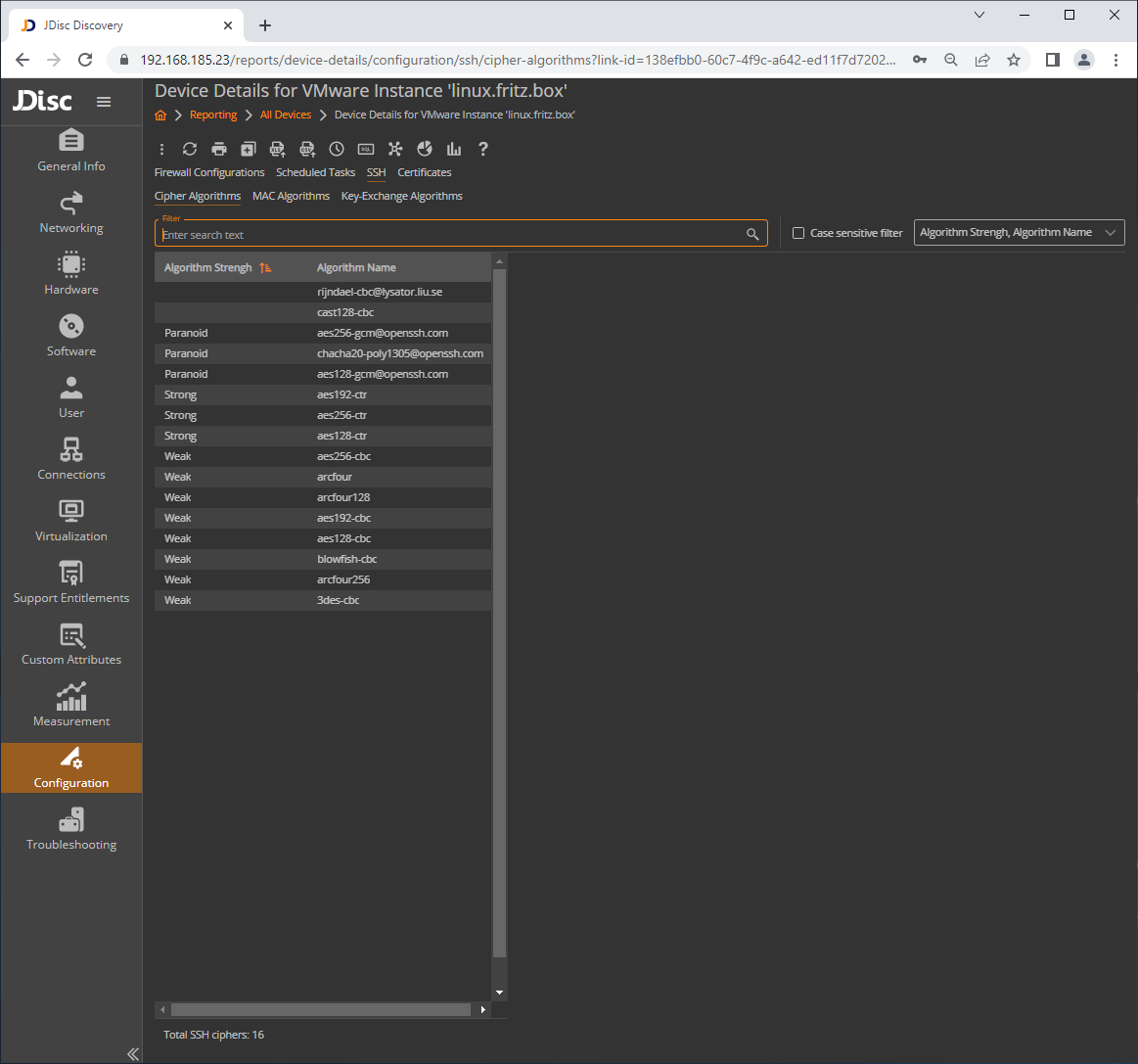
Once the data has been collected, you can review the list of available algorithms within the configuration section within the device details:
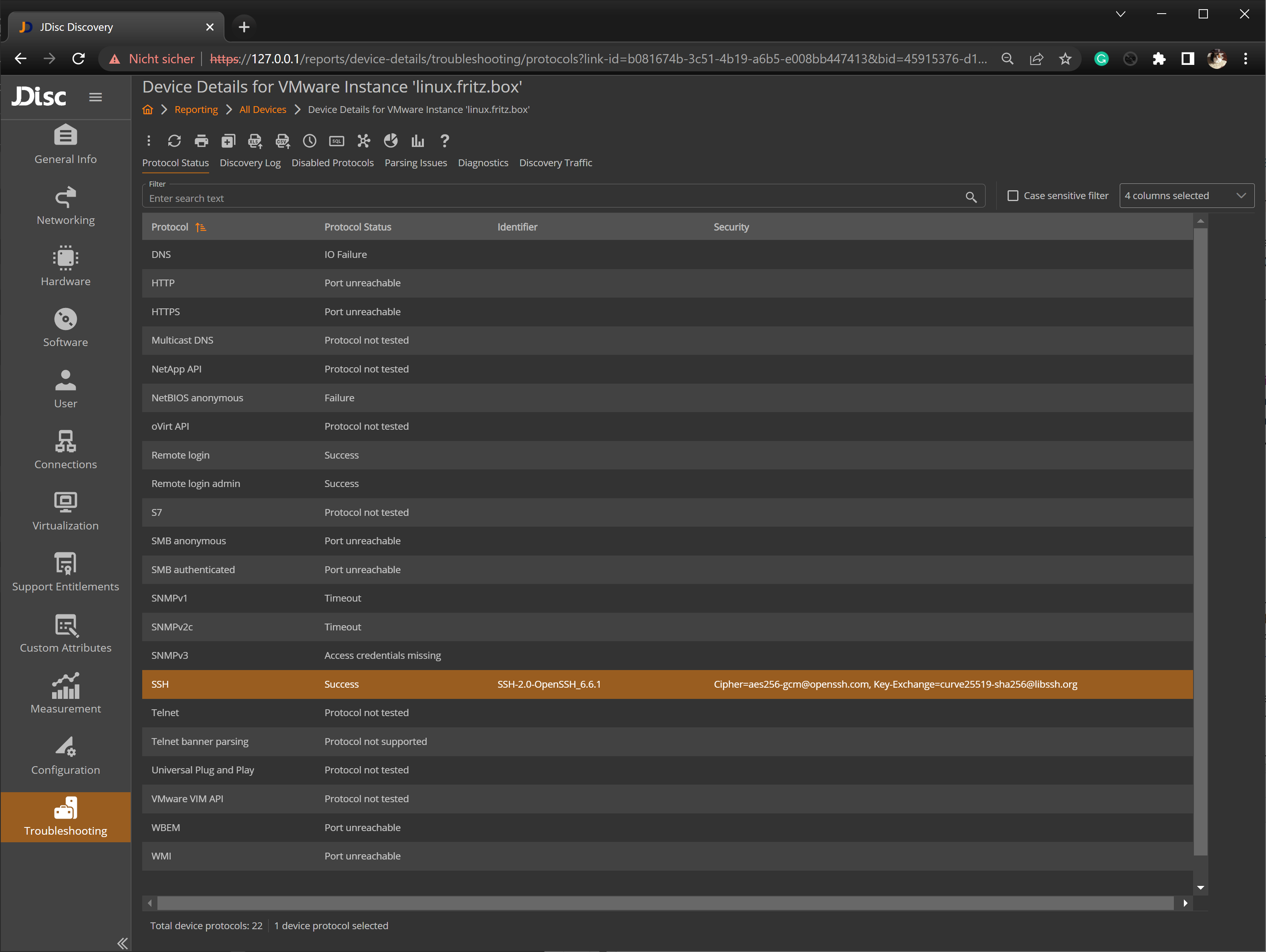
In addition to the algorithms that are offered by the SSH server, we also obtain the actual algorithm used to establish the connection. Those algorithms get stored together with the SSH protocol status:
Be aware that we need to initiate the protocol negotiation to obtain the list of available algorithms on the remote side. Just initiating the protocol negotiation without a subsequent authentication request (with a password or SSH key) might trigger intrusion detection systems. If that is the case, you might disable the discovery of SSH algorithms.
We hope you like that new feature…
Stay tuned
Thomas
