Web UI – JDisc Diagrams – A new way to visualize discovery data
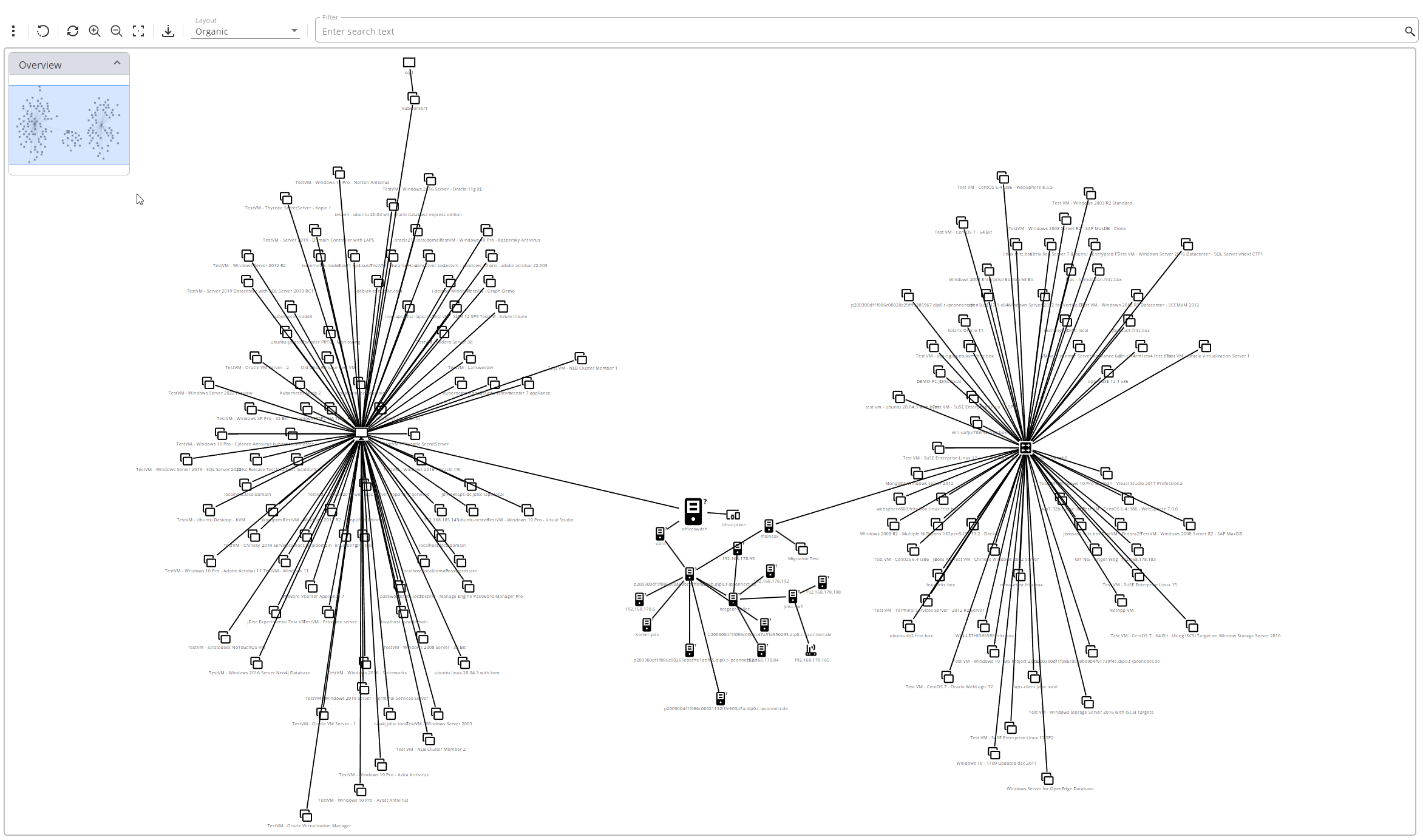
Dear JDisc friends, with JDisc Discovery release 5199, we have introduced a new set of features in our Web UI to support diagrams. In addition to the classic built-in reports, the diagrams offer a new way to view and navigate JDisc Discovery data. The main building blocks of JDisc diagrams are the entities. Such entities[...]
Read More